Many healthcare providers have shifted to electronic health records (EHRs). Compared to paper-based systems, EHR systems offer greater information recency and accessibility to patient records. Before switching to EHR systems, your practice must first understand the following.
The pros and cons of EHR systems
Comparing BYOD and CYOD
Enhance your business website with these design trends

Having a well-designed website is essential to any business, as it helps make a good first impression on customers, generate leads, and increase conversions. Enhance your business's website by following these tips.
Custom illustrations
A popular website design trend is the use of custom illustrations instead of photography.
Watering hole attack: What it is and how to protect against it

Watering hole attacks have become more common in recent years and pose a serious threat to organizations everywhere. Read on to learn more about what watering hole attacks and how your business can stay one step ahead of cybercriminals.
How watering hole attacks work
The term “watering hole” colloquially refers to a social gathering place where a particular group of people often go to.
How to make your computer last longer
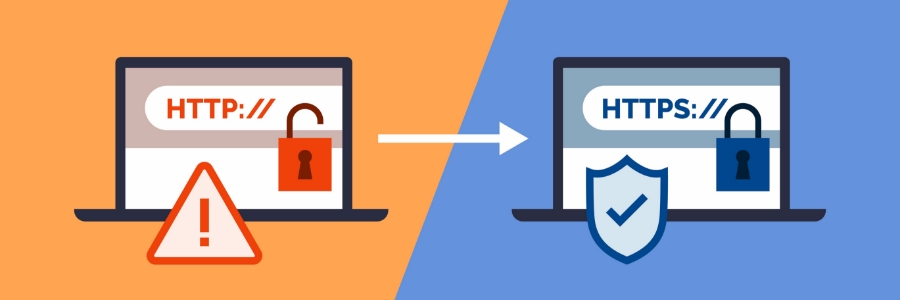
The S in HTTPS: What it is and why you should care
How to improve your online security: Tips for safe surfing
HIPAA compliance guidelines for social media usage

Social media can be a powerful tool for healthcare organizations to spread awareness. But in using social media, these organizations must adhere to specific Health Insurance Portability and Accountability Act (HIPAA) compliance standards. In this blog post, we will discuss guidelines for HIPAA compliance regarding the use of social media.
7 PC energy-saving tips
Here’s how to avoid security threats on the web

Malicious actors wait in the virtual shadows while you do internet searches, scroll through your social media feeds, or use company apps online. Just by browsing the web, your workers increase the risk of exposing sensitive and critical data, which is why everyone in your organization must learn how to avoid cyberthreats.